Network Security
Research Areas
- Real Time Bursty Flow Detection
- Mitigation of Distributed Denial of Service Attacks
- Capability-based Approach
- Rerouting-based Approach
- Novel Attacks
- Security in Software Defined Networks
Meeting Schedule
Group meetings are held once a week during the semester.
Highlighted
ALBUS: A Probabilistic Monitoring Algorithm to Counter Burst-Flood Attacks
This motive behind this study is to defend against burst-flood attacks, volumetric DDoS attacks characterized by swarms of medium-rate sub-second traffic bursts, that successfully evade classical probabilistic monitoring algorithms. Since attacks using a low number of high-rate long-lived flows may be detected rapidly, most DDoS attacks today rely on medium rate short-lived flows.
Classic probabilistic monitoring algorithms like CountMin-Sketch and CountSketch monitor flows within limited memory and report flows that violate a volume threshold. However, they are not robust enough against burst-flood attacks due to the tradeoff between recall and precision when configuring a threshold and an unpredicatable dependency between reset periods and the variable burst widths of the attacks.
This study proposes ALBUS (Adaptive Leaky-Bucket Undulation Sensor), which leverages shared counters to continuously select flows to be precisely monitored. This makes it effective at detecting bursts without reporting legitimate flows. In addition, ALBUS avoids resets and applies filtering techniques to improve the accuracy of the detected bursts.
ALBUS scales up to high traffic rates as demonstrated with an FPGA implementation. It can be easily integrated into modern DDoS defense systems by means of a P4 implementation.
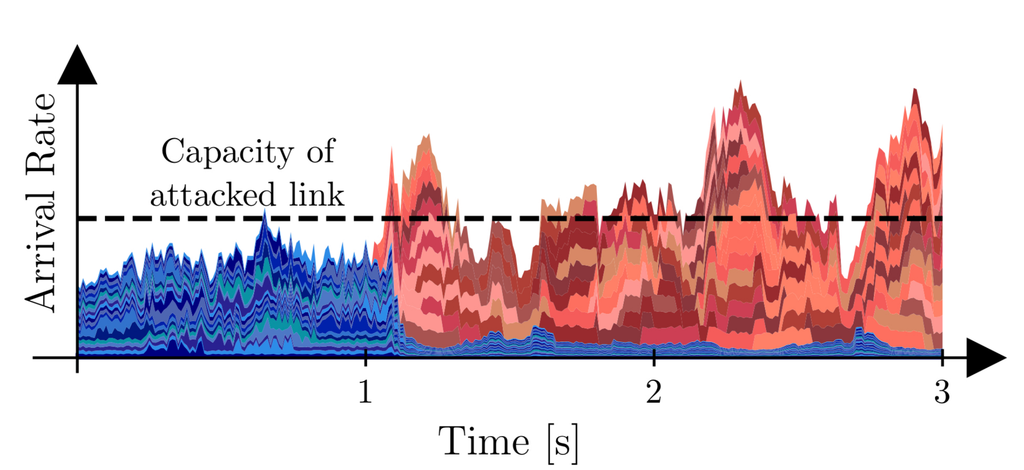 |
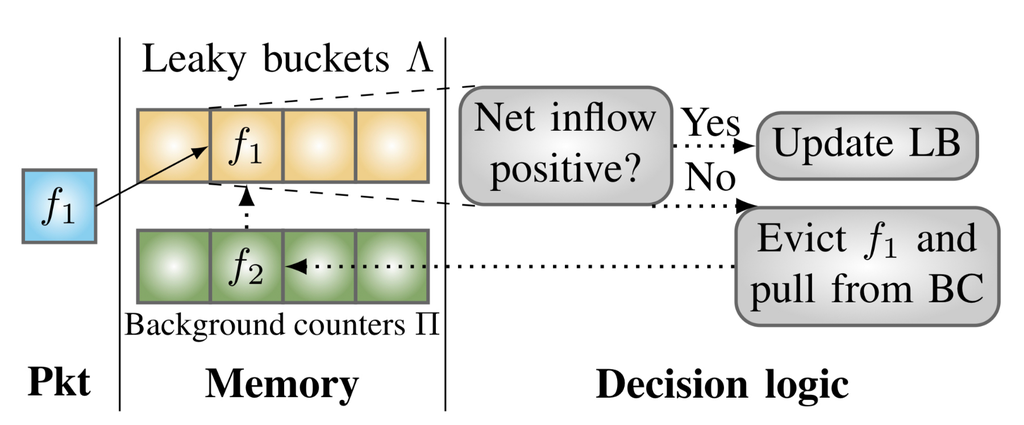 |
|---|---|
| Burst Flood Attack | ALBUS Basic Design |
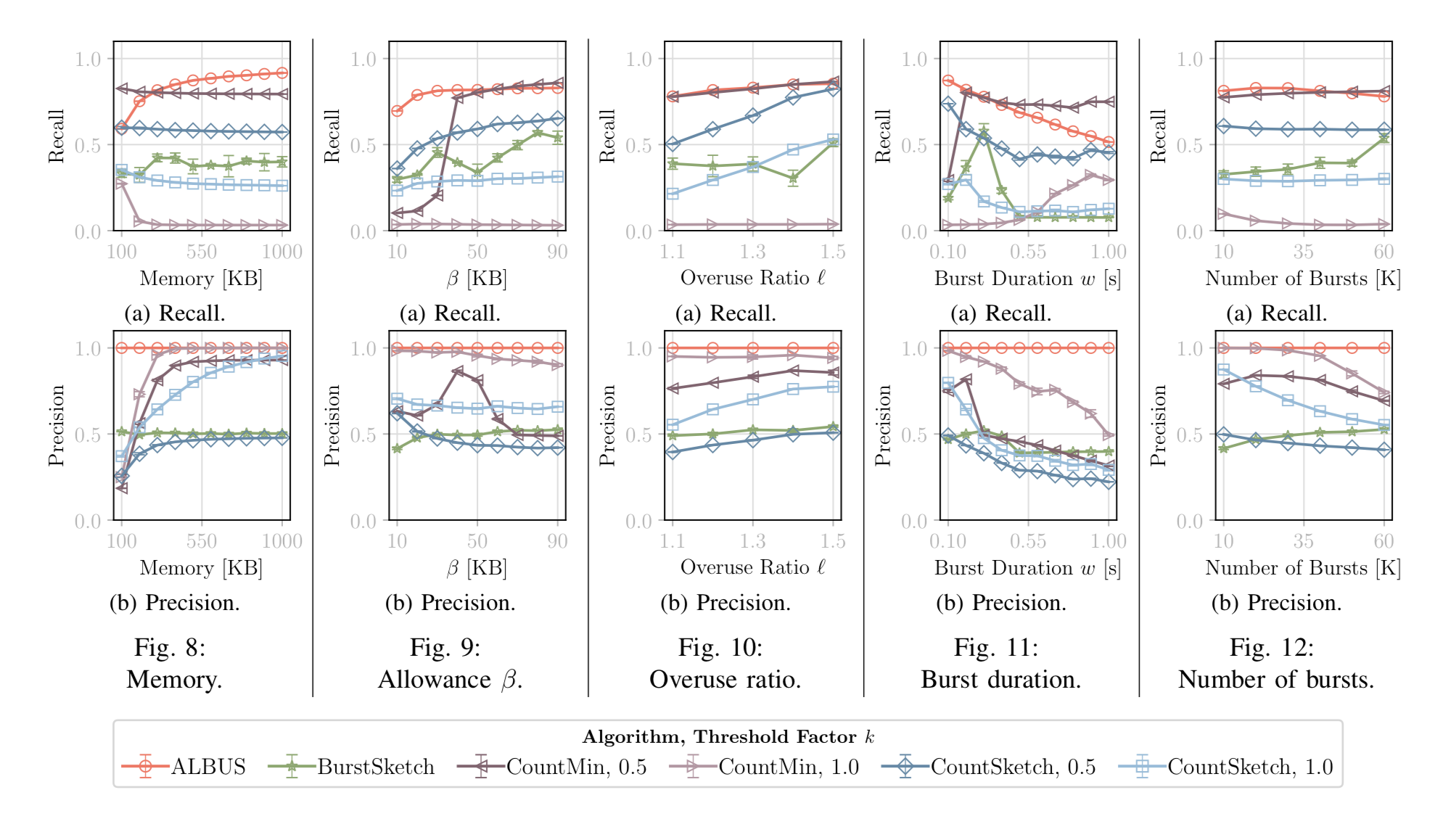 |
|---|
| ALBUS Results |
On the Feasibility of Rerouting-based DDoS Defenses
A recent proposal against transit-link flooding attacks called routing around congestion (RAC) attempts to offer strong end-to-end availability to a selected critical flow by dynamically rerouting it to an uncongested detour path without requiring any inter-AS coordination. The defense relies only on a well-known BGP inbound route-control mechanism.
This study presents an analysis of the infeasibility of the RAC defense. To be effective, the RAC solution must satisfy both of the following properties: (1) guarantee the establishment of an arbitrary detour path of its choice (2) isolate the established detour path from non-critical flows, so that the path is exclusive to its critical flow. However, this study reveals a tradeoff between the two properties. When an arbitrary detour path is not guaranteed, it is difficult for the RAC defense to be effective. However, even if a detour path can be established, the lack of complete path isolation limits the bandwidth availability of the detour path since non-critical flows must share the path with the critical flow. In addition, it is proved that the inability to satisfy both properties renders the RAC defense not only ineffective but also unusable in practical settings.
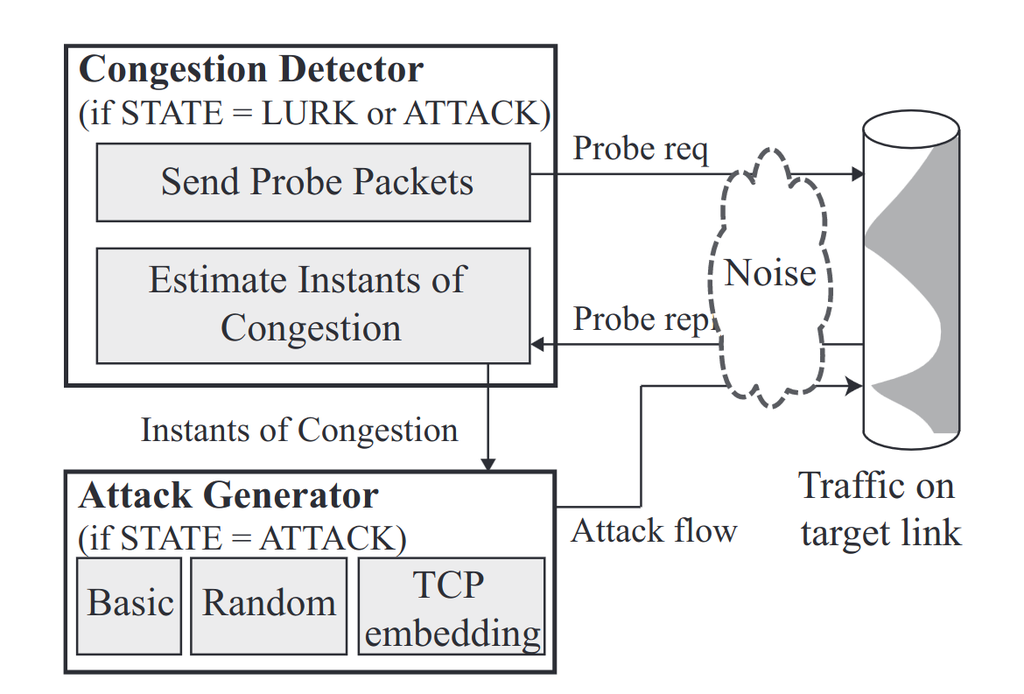
CICADAS: Congesting the Internet with Coordinated And Decentralized Pulsating Attacks
This study stems from the premise that we need to break away from the “reactive” cycle of developing defenses against new DDoS attacks (e.g., amplification) by proactively investigating the potential for new types of DDoS attacks.
Our specific focus is on pulsating attacks, a particularly debilitating type that has been hypothesized in the literature. In a pulsating attack, bots coordinate to generate intermittent pulses at target links to significantly reduce the throughput of TCP connections traversing the target. With pulsating attacks, attackers can cause significantly greater damage to legitimate users than traditional link flooding attacks.
To date, however, pulsating attacks have been either deemed ineffective or easily defendable for two reasons: (1) they require a central coordinator and can thus be tracked; and (2) they require tight synchronization of pulses, which is difficult even in normal non-congestion scenarios.
Our project argues that, in fact, the perceived drawbacks of pulsating attacks are in fact not fundamental. We develop a practical pulsating attack called CICADAS using two key ideas: using both (1) congestion as an implicit signal for decentralized implementation, and (2) a Kalman-filter-based approach to achieve tight synchronization. We validate CICADAS using simulations and wide-area experiments. We also discuss possible countermeasures against this attack.
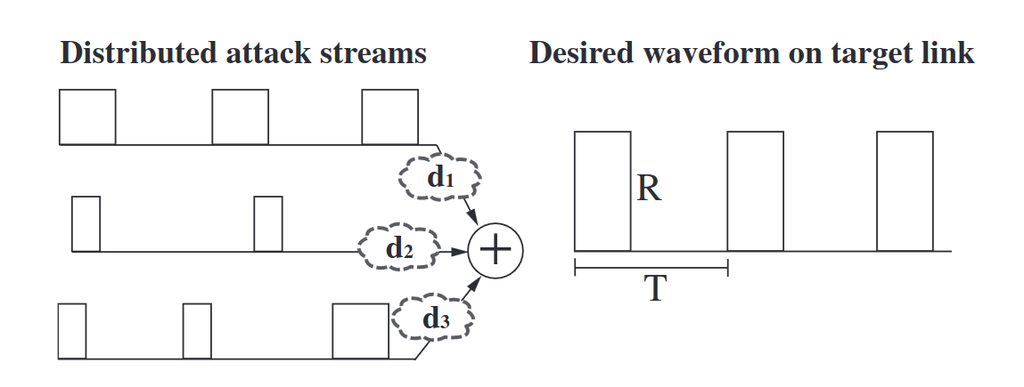 |
 |
|---|---|
| CICADAS Attack | CICADAS Overview |
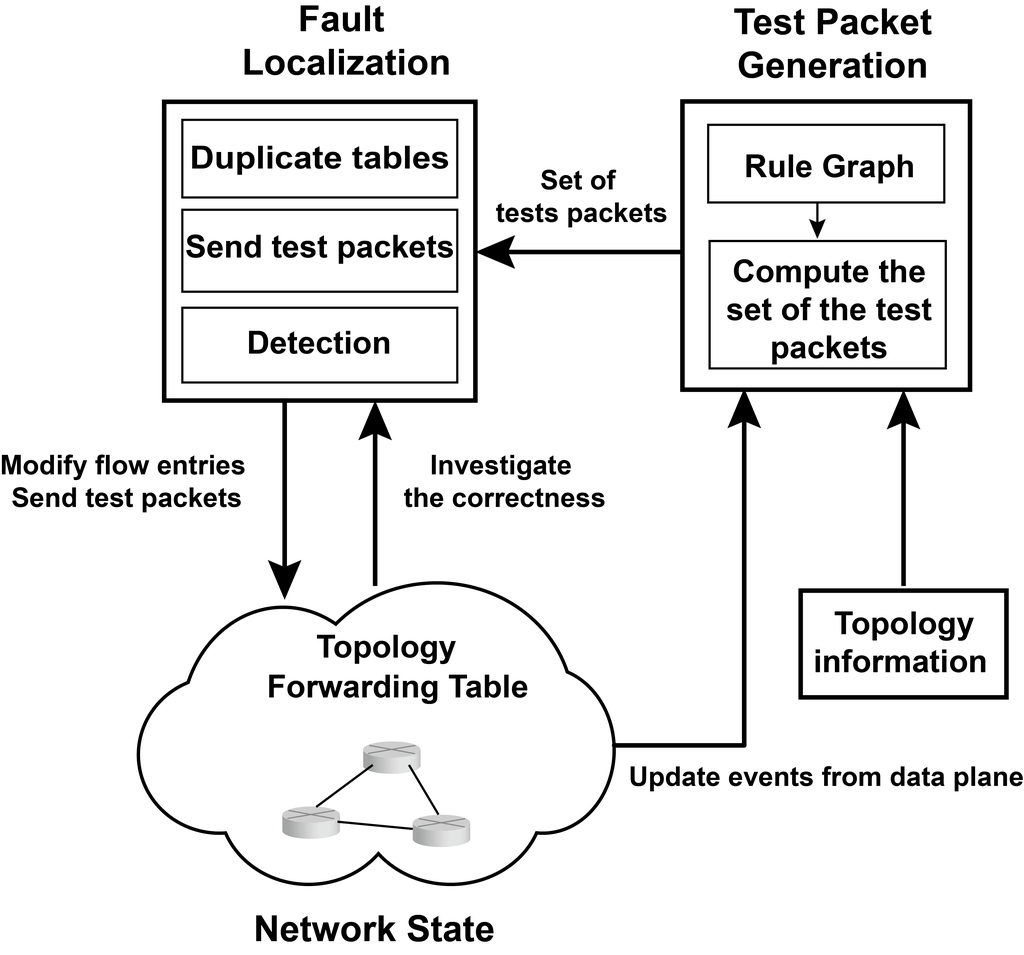
SDNProbe: Lightweight Fault Localization in the Error-Prone Environment
Efficiently and correctly localizing malicious SDN switches whose behavior deviates from the controller’s intent is a daunting challenge, and existing network troubleshooting tools can easily misdetect the mismatch between the actual behavior of malicious switches and the operator’s intent.
In this paper, we propose SDNProbe, a lightweight SDN application that sends minimized number of probe packets to pinpoint misbehaving or malfunctioning switches. Similar to existing tools, the controller sends test packets to validate whether flow entries are correctly executed. To achieve low network overhead and fast detection, we propose an algorithm to provably minimize the number of test packets required to cover every flow entry in the network. To prevent circumvention from strong adversaries (e.g., know the detection algorithm or collude), we further extend the algorithm to randomize the test paths.
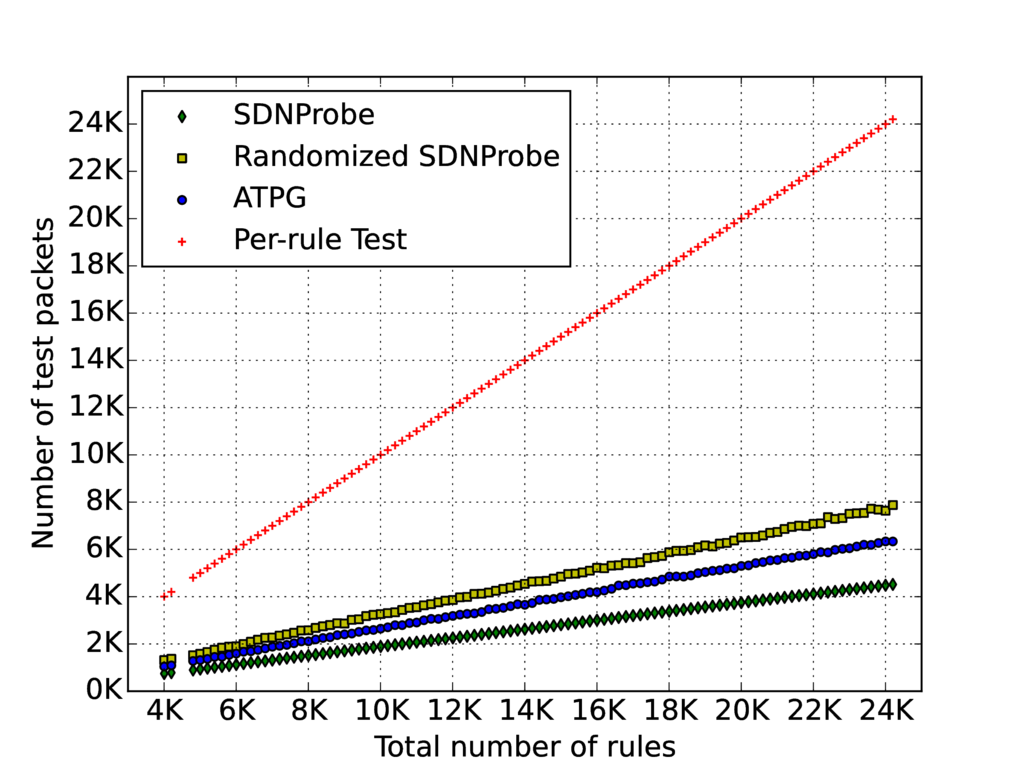
Based on realistic topologies and flow rules, our evaluation results confirm that SDNProbe can rapidly localize malicious switches by sending a minimal number of test packets. SDNProbe reduces the number of test packets required to localize all existing malicious switches by 30% compared to the state of the art technology. Hence, in addition to SDN’s support to a systematic and automatic network troubleshooting workflow, our work can further secure the workflow against in-network adversaries with significantly reduced overhead.
 |
 |
|---|---|
| SDBProbe Overview | SDNProbe Results |
Publications
Conferences and Workshops
- ALBUS: a Probabilistic Monitoring Algorithm to Counter Burst-Flood Attacks. S. Scherrer, J. Vliegen, A. Sateesan, H.-C. Hsiao, N. Mentens, A. Perrig In International Symposium on Reliable Distributed Systems, September, 2023.
- Low-Rate Overuse Flow Tracer (LOFT): An Efficient and Scalable Algorithm for Detecting Overuse Flows. [preprint] S. Scherrer, C.-Y. Wu, Y.-H. Chiang, B. Rothenberger, D. Asoni, A. Sateesan, J. Vliegen, N. Mentens, H.-C. Hsiao, A. Perrig In International Symposium on Reliable Distributed Systems, September, 2021.
- Speed Records in Network Flow Measurement on FPGA. A. Sateesan, J. Vliegen, S. Scherrer, H.-C. Hsiao, A. Perrig, and N. Mentens In International Conference on Field-Programmable Logic and Applications (FPL), August 2021.
- On the Feasibility of Rerouting-based DDoS Defenses. M. Tran, M. S. Kang, H.-C. Hsiao, W.-H. Chiang, S.-P. Tung and Y.-S. Wang In IEEE Symposium on Security and Privacy (IEEE S&P), May 2019.
- CLEF: Limiting the Damage Caused by Large Flows in the Internet Core. H. Wu, H.-C. Hsiao, D. E. Asoni, S. Scherrer, A. Perrig, Y.-C. Hu In International Conference on Cryptology and Network Security (CANS), September 2018.
- SDNProbe: Lightweight Fault Localization in the Error-Prone Environment. [code] Y.-M, Ke, H.-C. Hsiao, T. H.-J. Kim In IEEE International Conference on Distributed Computing Systems (ICDCS), July 2018.
- DAMUP: Practical and Privacy-aware Cloud-based DDoS Mitigation. [code] S.-C. Lin, P.-W. Huang, H.-Y. Wang, H.-C. Hsiao In IEEE/IFIP Workshop on Security for Emerging Distributed Network Technologies (DISSECT), April 2018.
- Migrant Attack: A Multi-resource DoS Attack on Cloud Virtual Machine Migration Schemes. J.-R. Yeh, H.-C. Hsiao, A.-C. Pang In 11th Asia Joint Conference on Information Security (AsiaJCIS), August 2016.
- Securing Data Planes in Software-Defined Networks. T.-W. Chao, Y.-M. Ke, B.-H. Chen, J.-L. Chen, C. J. Hsieh, S.-C. Lee, H.-C. Hsiao. In IEEE International Workshop on Security in Virtualized Networks (Sec-VirtNet), June 2016.
- CICADAS: Congesting the Internet with Coordinated And Decentralized Pulsating Attacks. Y.-M. Ke, C.-W. Chen, H.-C. Hsiao, A. Perrig, V. Sekar. In ACM Asia Conference on Computer and Communications Security (ASIACCS), May 2016.
- SIBRA: Scalable Internet Bandwidth Reservation Architecture. C. Basescu, R. M. Reischuk, P. Szalachowski, A. Perrig, Y. Zhang, H.-C. Hsiao, A. Kubota, J. Urakawa. In Networked & Distributed System Security Symposium (NDSS), February 2016.
- A Practical System for Guaranteed Access in the Presence of DDoS Attacks and Flash Crowds. Y.-H. Kung, T. Lee, P.-N. Tseng, H.-C. Hsiao, T. H.-J. Kim, S. B. Lee, Y.-H. Lin, and A. Perrig. In IEEE International Conference on Internet Protocols (ICNP), November 2015.
- Efficient Large Flow Detection over Arbitrary Windows: An Algorithm Exact Outside An Ambiguity Region. H. Wu, H.-C. Hsiao, and Y.-C. Hu. In ACM Internet Measurement Conference (IMC), November 2014.
Posters and Extended Abstracts
- Poster: Protecting Campus Networks with Cost-effective DDoS Defense. W.-H. Chiang, S.-P. Tung, Y.-S. Wang, I-J. Hsiao, H.-C. Hsiao In IEEE Symposium on Security and Privacy (IEEE S&P), May 2019.
- Challenges in Realizing Privacy-aware Cloud-based DDoS Mitigation Mechanism. S.-C. Lin, W.-N. Chen, H.-C. Hsiao In USENIX Security Symposium Poster Session, August 2018.